Table of Contents
- Getting Started
- Agent-Based Management
- Common Tasks
- Data Providers
- Directory Services
- Auditing
- Hosts
- Templates
- Template Properties
- Batch Update Templates
- Assign Templates
- Log Management Templates
- SCAP Compliance Monitor
- Active Directory User Monitor Templates
- File and Directory Monitor Templates
- Windows Monitor Templates
- CPU Monitor Template
- Memory Monitor Template
- Disk Space Monitor Template
- Account Lockout Monitor Template
- Audit Policy Monitor Template
- Logon As Monitor Template
- Logon Monitor Template
- Performance Counter Monitor Template
- PowerShell Template
- Process Monitor Template
- RDP Session Monitor Template
- Registry Value Monitor Template
- Service Monitor Template
- SMART Disk Monitor Template
- System Security Monitor Template
- Windows Update Template
- WMI Query Template
- Task Scheduler Template
- Clock Synchronization Template
- Defragment NTFS Disks Template
- Network and Application Monitor Templates
- SSL Certificate Monitor Templates
- Database Templates
- Email Monitor Templates
- SNMP Monitor Templates
- Windows Accounts Templates
- Monitors
- Reports
- Auto-Configurators
- Filters
- Actions
- Schedules
- Environment Variables
- Options
- SNMP
- SSH Shell
- Syslog
- System Reset
- Shared Views
- Active Directory User and Group Filters
- Assign Actions
- Assign Azure Audit Logs
- Assign Consolidated Logs
- Assign Directories
- Assign Disks
- Assign Event Logs
- Assign Files
- Assign Services
- Assign Shares
- Auto-Config Host Assignment Properties
- Define CSV and W3C Log Entry Columns
- Define Log Entry Columns
- Define Log Entry Columns with Regular Expressions
- Executable Status
- Executable Timeline
- Explicitly Assigned Logs
- File Explorer
- General Executable Properties
- Report Columns
- Report Date/Time Ranges
- Report Security Event Log Filters
- Select Folder or File
- Target Files and Sub-Directories
- Command Line Interface
- Server Configuration
- Agent Configuration
- Troubleshooting
- Best Practices
- Terminology
Event Log Archiving for JSIG and CMMC Compliance
Hello this is Mike from Corner Bowl Software. In this tutorial I am going to show you how to save your Windows Event Logs for 5 years on a single air gapped machine, a common requirement for JSIG and CMMC compliance.
In this Topic
Video Tutorial

What is Event Log Archiving?
Event Log Archiving is the process of backing up and clearing Windows Event Logs then moving archived Event Log files to a central location or FIPS compliant storage device for future auditing and review.
So why would you want to save your Windows Event Logs for 5 years?The main purpose is for compliance, otherwise our log consolidation to SQL Server or MySQL is going to be far superior for deep analysis and reporting purposes. If your organization is not required to archive the native Event Log files, please see our Event Log Consolidation Tutorial Series.
How Does it Work?
To save Event Log files on a single air gapped machine, Corner Bowl executes built-in Windows functions to archive, clear and move backed up Event Logs, specifically Local WMI.
How To Configure Event Log Archiving
- From the root Templates Node, expand Sample Templates / NIST/JSIG / Windows / Agentless.
- Once expanded, you will see 2 Event Log Backup Templates. The first, AU-2/11: Event Log File Backup (Air Gapped Single Machine) includes a post backup Action that not only Archives the Event Log File locally but also saves the Event Log File to removable media. The other template, AU-2/11: Event Log File Backup (Application, Security, System) is identical, however, does not include the Action to save the Event Log File to removable media. For this tutorial, I am going to select the Template that does not include the extra post backup Action.
- Right click on template then select Template Properties.
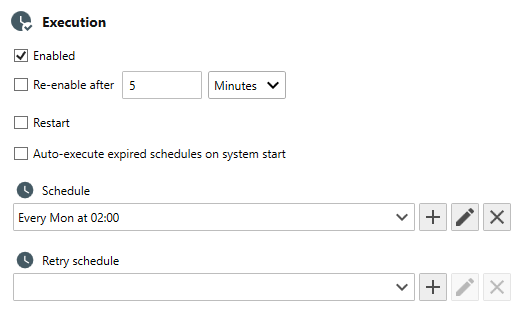
- Use the General Tab to set a schedule, for example, Every Monday at 02:00.
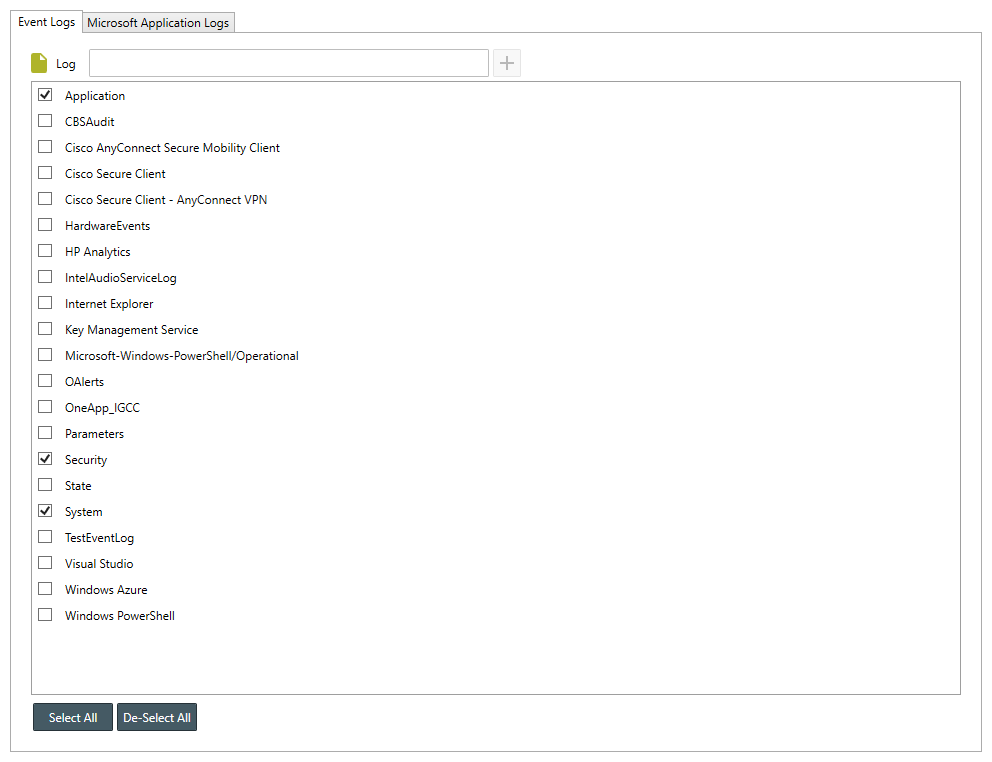
- Use the Logs Tab to select the target Event Logs and Microsoft Application Logs. By default, the Application, System and Security Event Log have been selected for you.
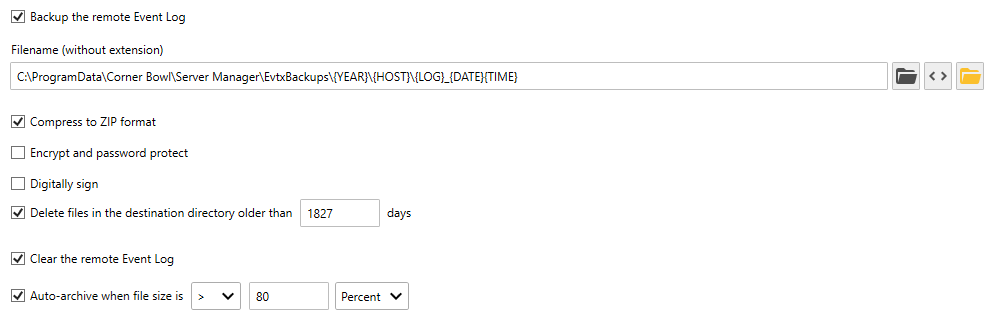
- Use the Options Tab, to specify the target location to save the files. The default is:C:\ProgramData\Corner Bowl\Server Manager\EvtBackups\{YEAR}\{HOST}\{LOG}_{DATE}{TIME}This setting saves the backups to a separate folder for each year and host and is the default for this Template type.
- Use the Compress option to zip the EVTX files. Optionally, choose to encrypt the files and password project them using FIPS compliant AES-256 encryption. If selected, Zip7 format is utilized, so you will need to download either Zip7 or another compatibility program to decompress the files outside of Corner Bowl.
- Optionally, you can digitally sign the files with a code signing certificate. If you choose to sign the files, you must use Corner Bowl to remove the signature before the files can be viewed.
- Use the Delete files in the destination directory option to remove the archives once they are older than 5 years.
- Next, notice the Clear flag is set by default as well as the Auto-archive option. Compliance requirements, such as JSIG and CMMC, require Windows is configured to auto-archive. Once set on Windows, log files that reach their maximum size are automatically backed up to Windows Event Logs directory which is:C:\Windows\System32\winevt\LogsWe want to avoid this scenario, otherwise we have to separately pull those log files. To avoid this scenario, the Auto-Archive option has been added which checks the Event Log file size once a minute. Once the threshold, in this case 80%, is reached, Corner Bowl automatically executes the optionally assigned Event Log Consolidation Templates so all the entries can be saved into the Log Consolidation Database for compliance Reporting, then the log file is archived and cleared avoiding the scenario where files are dumped into the operating system directory.
- Moving on, the Agent Tab is cleared because we are running this template on a single air gapped machine.
- Then finally, per section AU-5 in the JSIG specification, the Actions Tab includes a Desktop Notification action which displays a popup anytime there is a problem with the backup process. In the case of failure, you also have the option to view the built-in Errors Report found under the root Status Node.
- Next, use the Assignments View to assign this Template to the localhost.
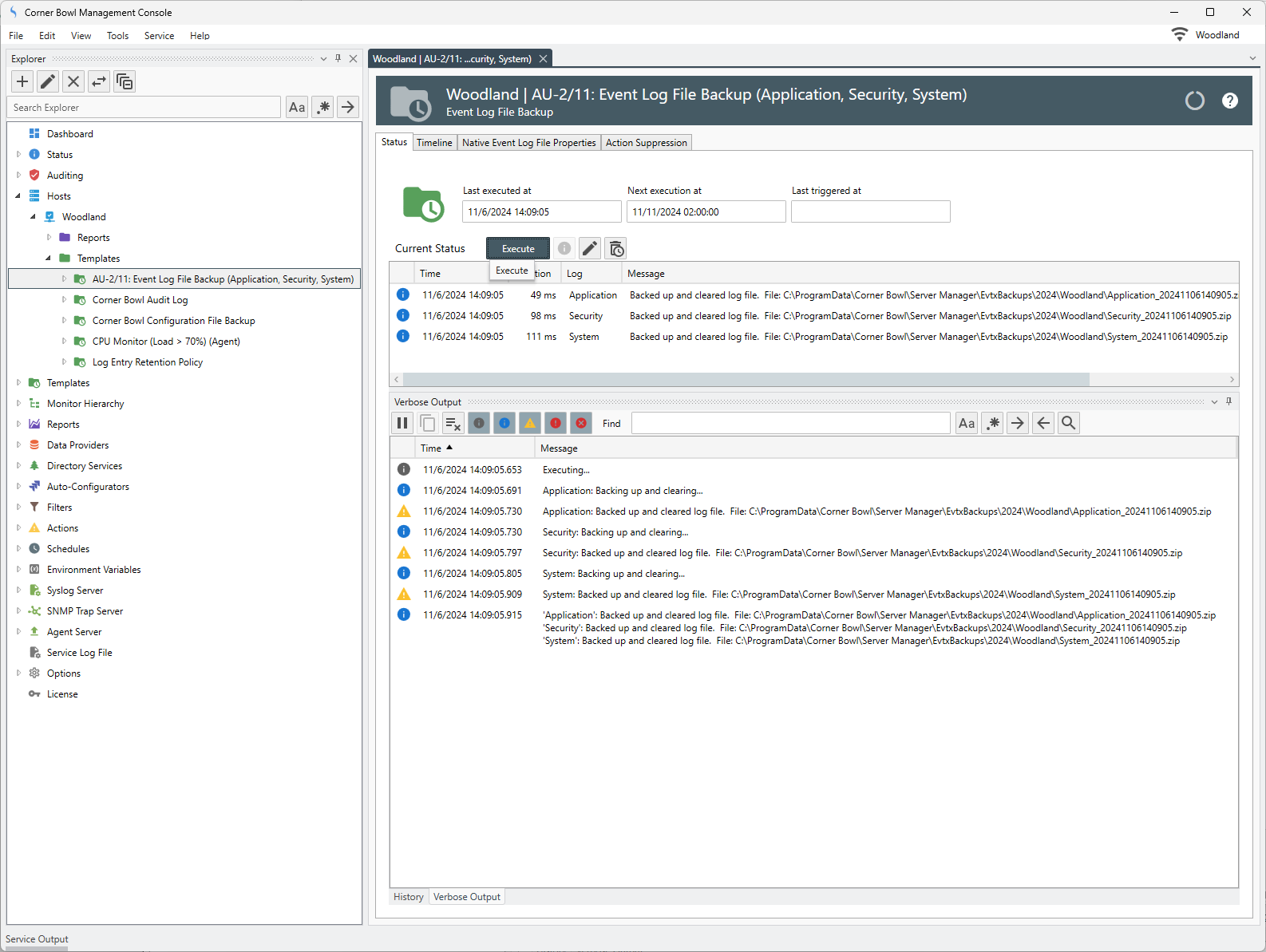
- Once assigned, find the Template under the localhosts’ Templates Node. Right click then select Execute Verbose. Selecting the Verbose Tab reveals the Event Log Consolidation Template is first executed followed by the backup process.
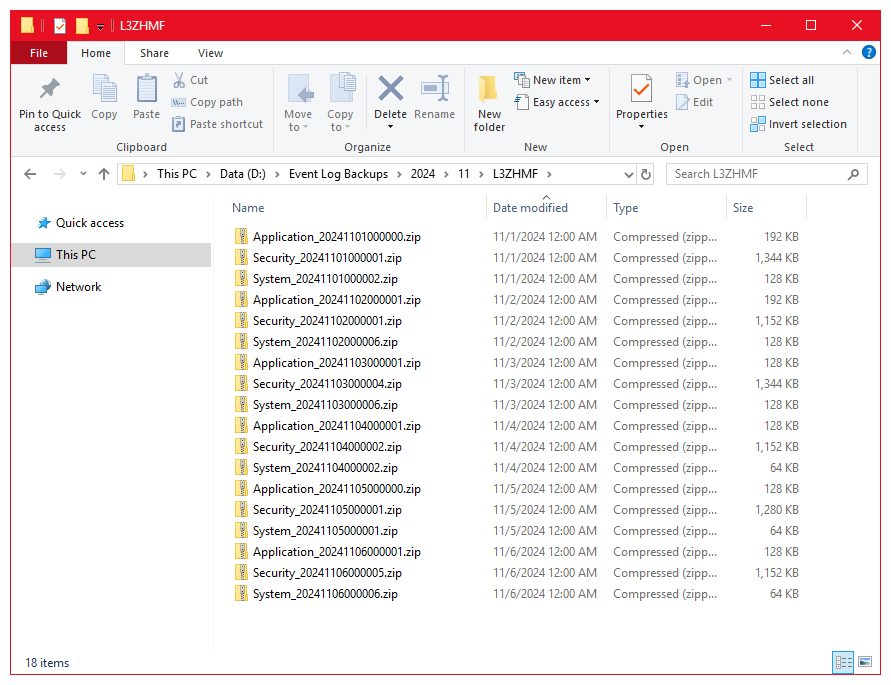
- Opening Windows Explorer reveals the backed up files. Copy or move these files to a FIPS compliant external storage device on a weekly basis.