Security Information and Event Management
SIEM | Log Collection | Log Retention | Log Monitoring
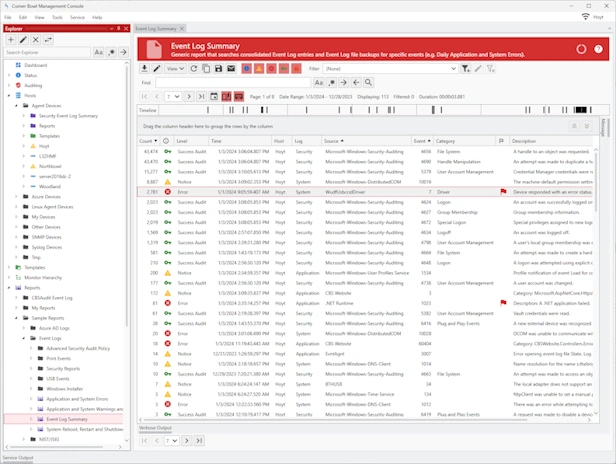
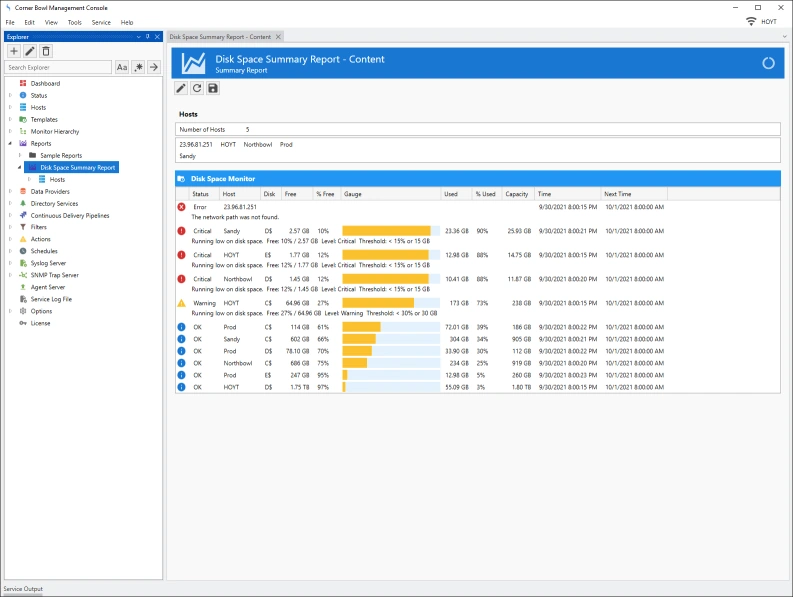
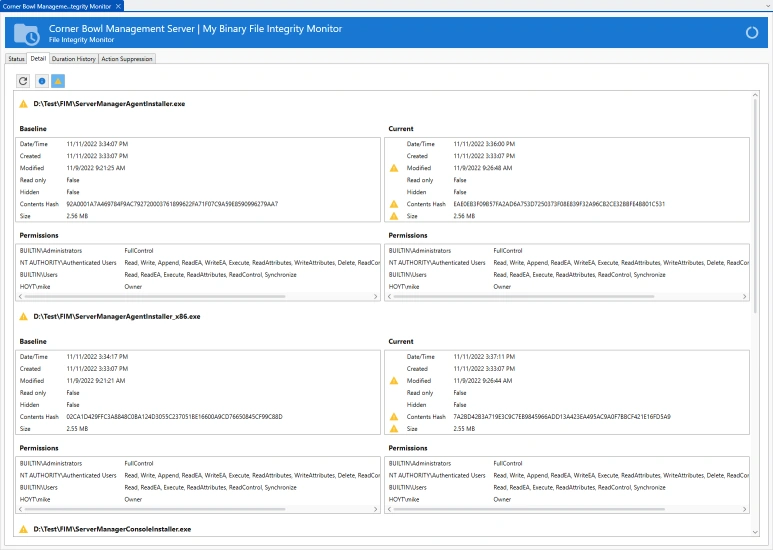
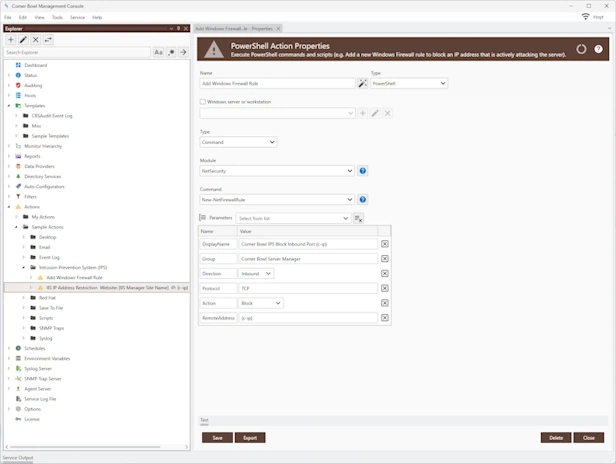
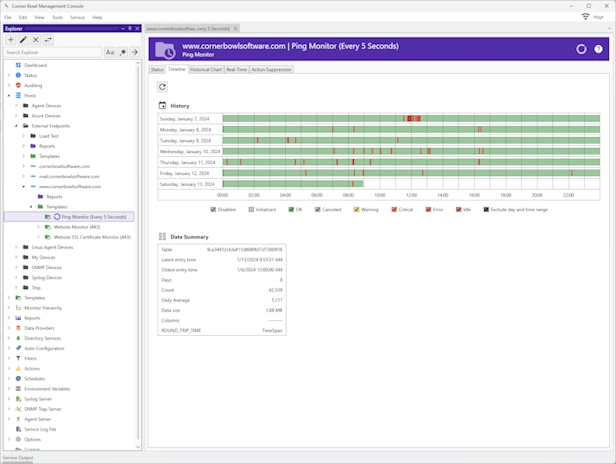
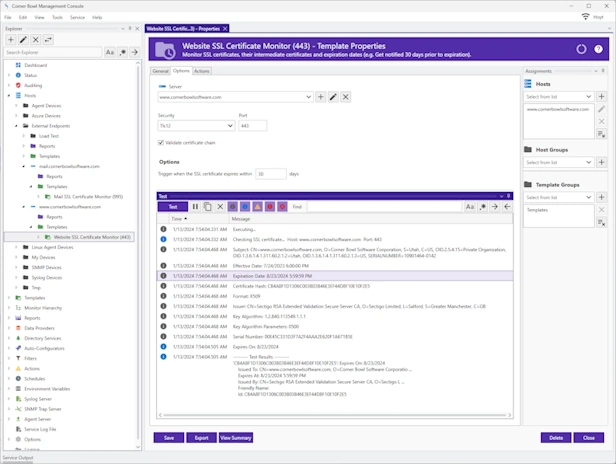
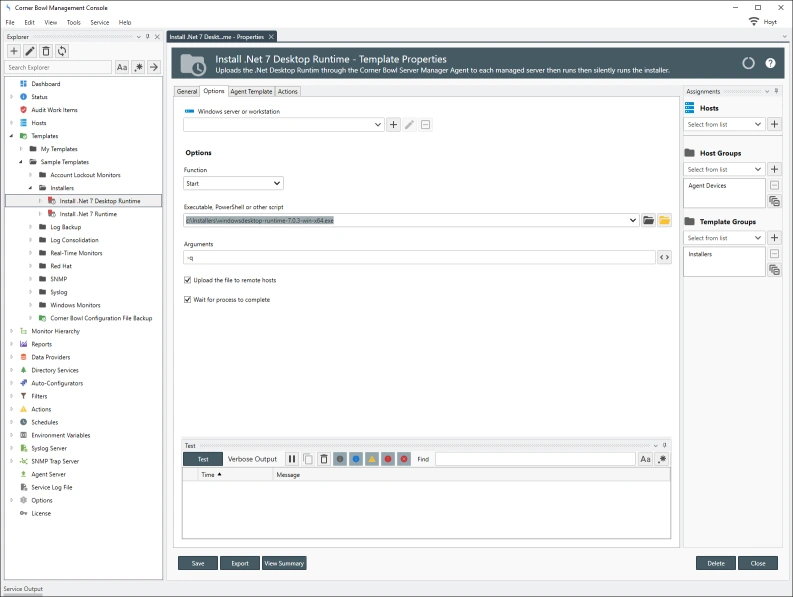
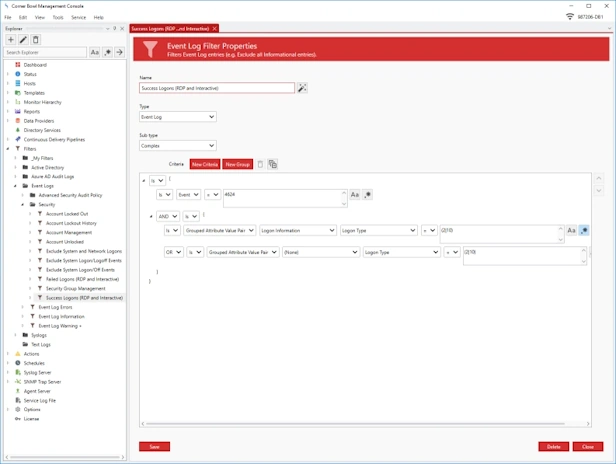
Manage Azure, Windows, Linux, Red Hat, Ubuntu and network hardware logs. Agent-based and agentless options for Windows and Linux. Batch Import and Audit Windows Event Log Files for CMMC and JSIG Compliance.