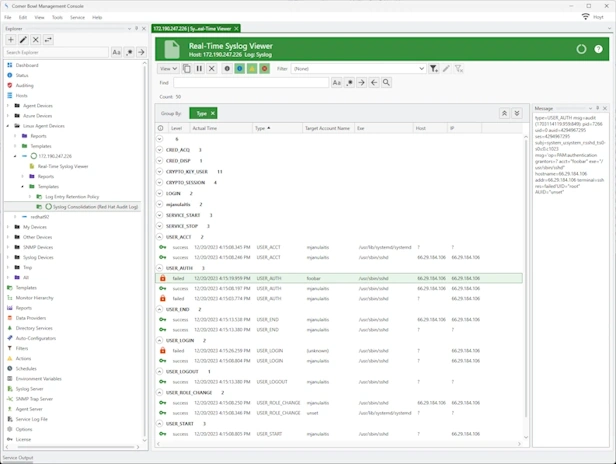
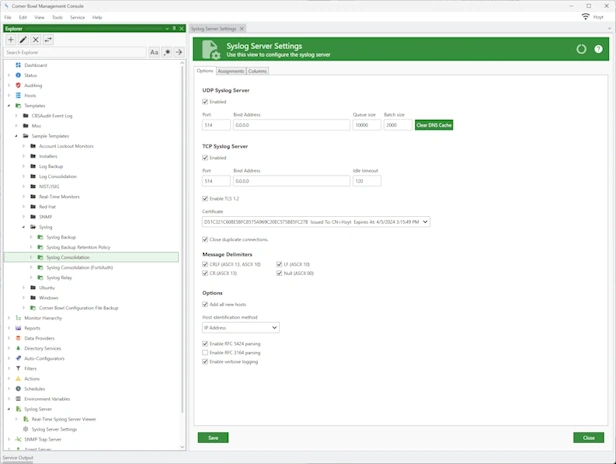
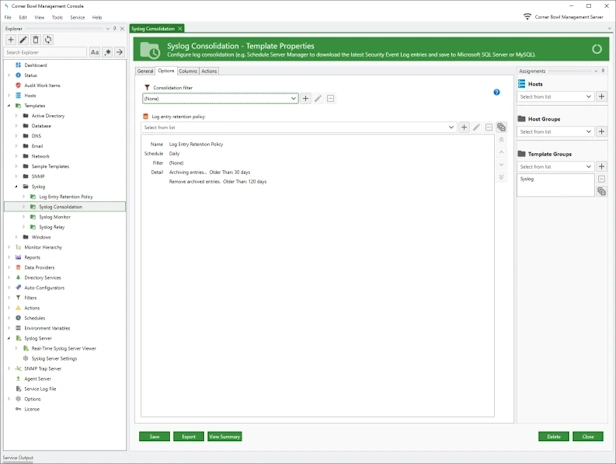
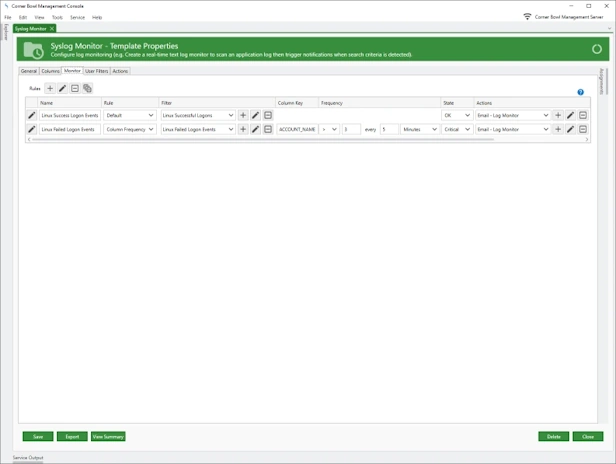
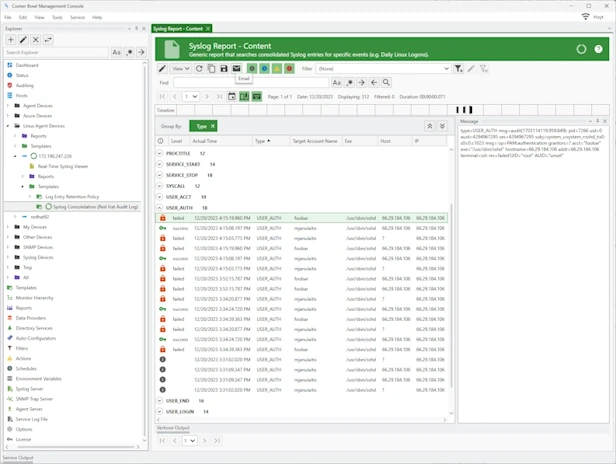
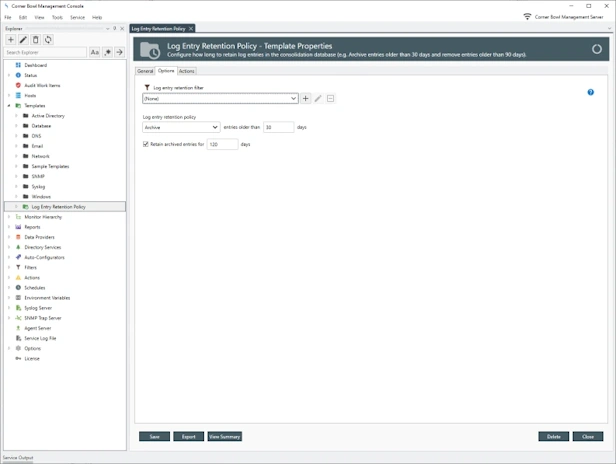
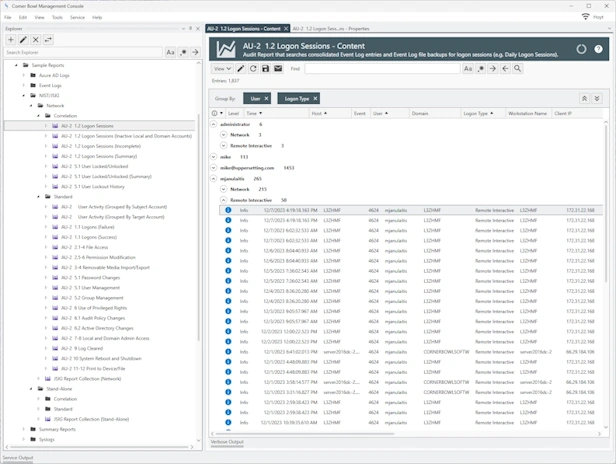
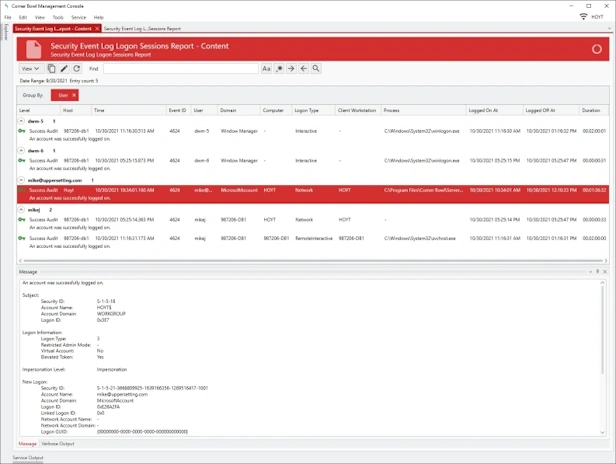
Quickly identify and resolve security issues cost-effectively with Corner Bowl Server Manager, featuring both Linux and Windows syslog servers. When cost is an issue, Corner Bowl Server Manager is the leading choice for Information Systems Security Managers managing the vast security event log data generated by network hardware devices such as gateways, switches, firewalls and Linux servers. This enterprise solution simplifies syslog management, offering capabilities such as syslog consolidation, archiving, retention, real-time monitoring, reporting, and the implementation of compliance controls and inline auditing, ensuring a comprehensive and compliant approach to network security.